5 new Google Cloud security solutions to quash cybersecurity threats
Syah Ismail2021-11-11T12:37:32+08:00In every industry, in every part of the world, cybersecurity concerns continue to grow in the wake of attacks on critical infrastructure and the software supply chain. Governments and businesses of all sizes recognize that they must do more to protect their employees, customers, and citizens.
Over the past year, Google Cloud has been delivering on its vision of Invisible Security for its customers, where capabilities are continuously engineered into both its cloud platform and products to bring the best of Google’s security to wherever your IT assets are. Now, Google wants to help organizations with their security transformation and offer even more ways to accelerate these essential improvements.
1. Google Cybersecurity Action Team

While access to the latest, most advanced security technology is important, the expertise of what it will take to become resilient in the face of today’s risk and threat environment is foundational.
The Google Cybersecurity Action Team marshals experts from across Google to form the world’s premier security advisory team. It has a singular mission to support the security and digital transformation of governments, critical infrastructure, enterprises, and small businesses.
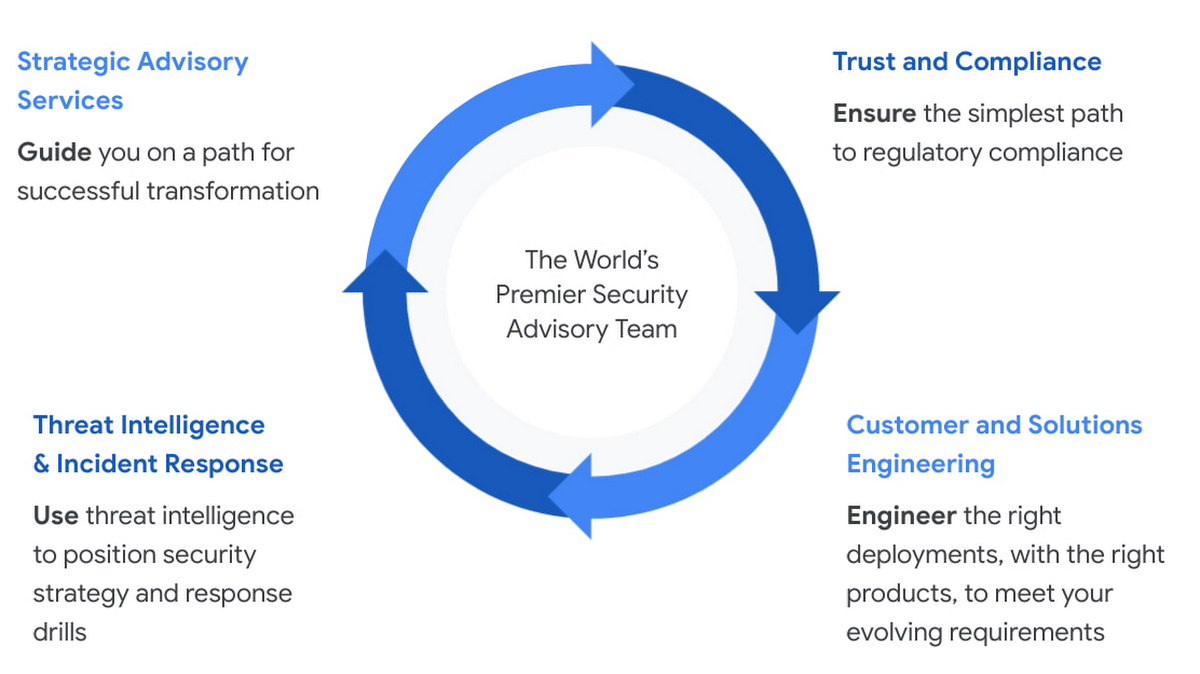
Building on existing security solutions engineering efforts, the Google Cybersecurity Action Team introduced a security and resilience framework that delivers a roadmap for a comprehensive security management program aligned with the National Institute of Standards and Technology’s Cybersecurity Framework using cloud technologies from Google Cloud and our partners.
Learn more about the Google Cybersecurity Action Team.
2. Google Work Safer

Bringing you the expertise and hands-on guidance to help with your security transformation is just one valuable step. Too many organizations can’t wait any longer to begin their modernization efforts – they need a new baseline, and they need it now.
That’s why Google Work Safer was introduced, designed to help organizations, their employees, and partners collaborate and communicate securely and privately in today’s hybrid work environment. Work Safer provides companies with access to best-in-class security for email, meetings, messages, documents, and more. It uniquely brings together the cloud-native, zero-trust solutions of Google Workspace with BeyondCorp Enterprise for secure access with integrated threat and data protection. For customers who want secure devices, Work Safer includes Pixel phones managed with Android Enterprise, Chrome Enterprise Upgrade, and HP Chromebooks. Customers can also leverage Google’s Titan Security Keys for account protection, reCAPTCHA Enterprise for website fraud prevention, Chronicle for security analytics, and a variety of migration services for a seamless transition.
The program is designed to meet the needs of all organizations, including small businesses, enterprises, and public sector institutions, many of which are reliant on legacy technology and often lack the expertise to fully address rising security challenges associated with hybrid work. Learn more about Google Work Safer.
3. Automatic DLP
Automatic DLP, now in preview, is a prime example of how Google is making Invisible Security a reality. It’s a game-changing capability that discovers and classifies sensitive data for all the BigQuery projects across your entire organization without you needing to do a single thing. Google is also introduced Ubiquitous Data Encryption, a solution that combines Google’s generally available Confidential Computing, External Key Management, and Cloud Storage products to seamlessly encrypt data as it’s sent to the cloud. Using your External Key Management solution, data can now only be decrypted and run in a confidential VM environment, greatly limiting potential exposure.
4. Cloud Build
Cloud Build is SLSA Level -1 compliant by default, with scripted builds and available provenance. With the new Build Integrity feature, Cloud Build automatically generates a verifiable build manifest that includes a signed certificate describing the sources that went into the build, the hashes of artifacts used, and other parameters. Additionally, Binary Authorization’s integration with Cloud Build makes it easy to set up deploy-time constraints. You can also now easily pair Binary Authorization with Cloud Run to ensure only trusted images make it to production. These integrations are now generally available.
5. Cloud Armor Bot Management
Cloud Armor Bot Management integrates Cloud Armor and reCAPTCHA Enterprise. You can enable protection without any server-side changes to your applications, and because detection and enforcement happen in-line, at the edge of Google’s network, you can mitigate threats before they have a chance to impact your applications, whether they run on GCP, on-premise, or in a hybrid or multi-cloud deployment.
These new security solutions are just a few examples of Google’s commitment to ensuring that every day, you are making your organization safer.





